ARP Vulnerabilities And Spoofing-Attacks.
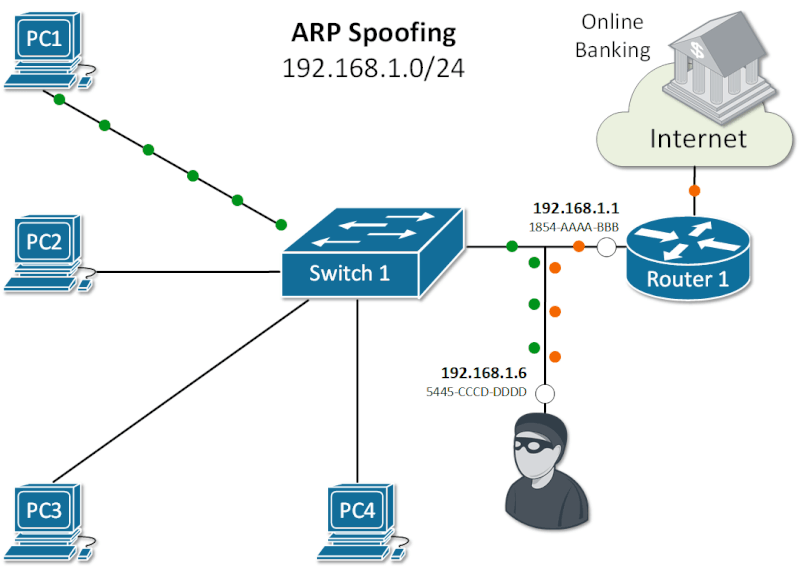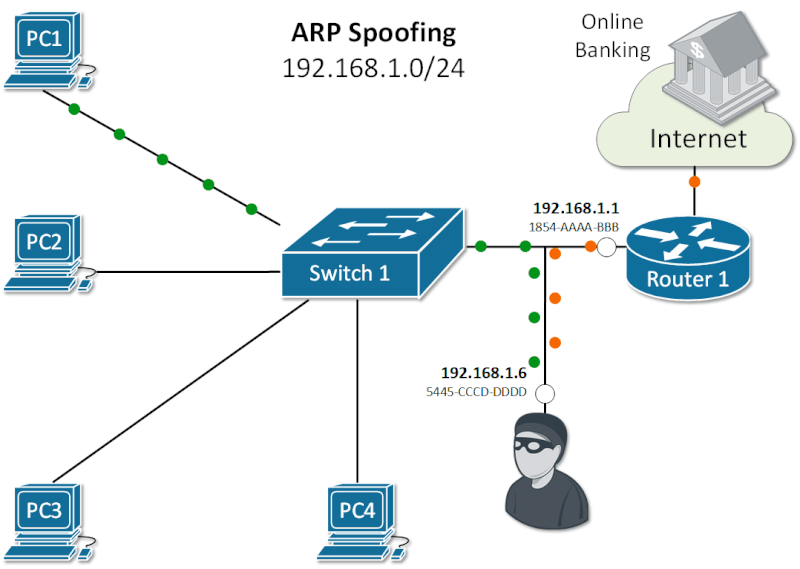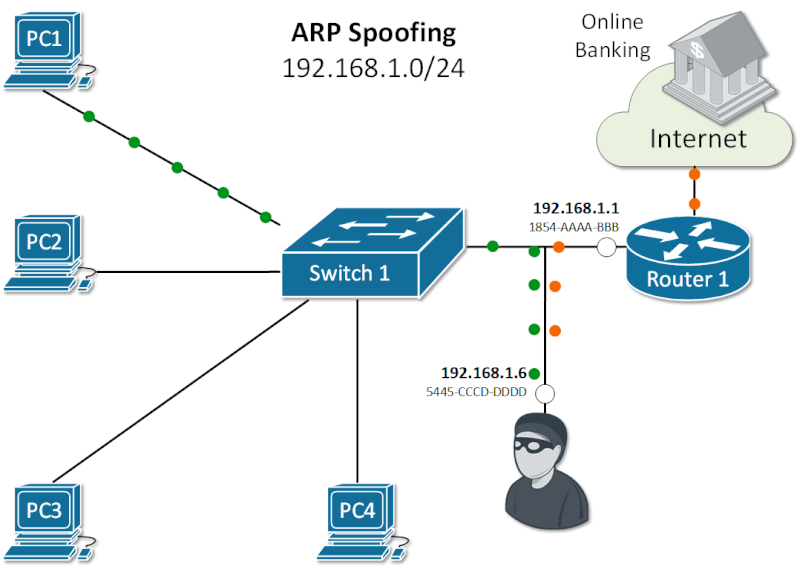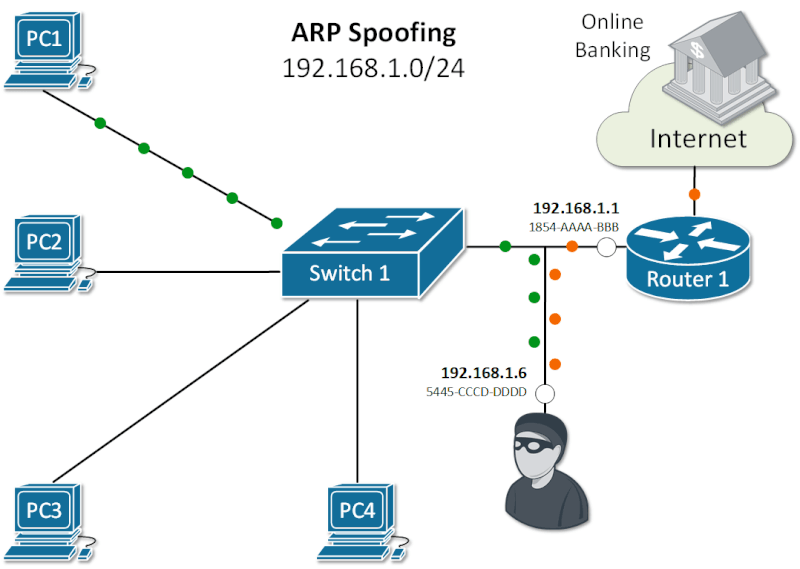
Exploiting ARP Vulnerabilities: Understanding ARP Spoofing and Its Security Risks.
ARP Vulnerabilities.
The Address Resolution Protocol (ARP) was created in an era when network security was minimal. As a result, ARP operates in plaintext and lacks built-in security features.
It does not validate incoming ARP packets, and it will accept ARP Responses even if no ARP Request was made.
There is no default mechanism to verify whether a rogue device is sending malicious ARP messages or intercepting and modifying ARP Requests and Replies.
This lack of validation makes ARP susceptible to attacks like ARP spoofing, where attackers position themselves in the data path to intercept and steal sensitive information.

