Restrict personal devices from accessing desktop applications such as Teams, OneDrive, etc., and troubleshoot any related issues.
April 04, 2025
You can utilize Conditional Access to restrict users based on factors like location, IP address, and more. In this guide, we'll focus on blocking access for users using personal devices.
- Go to Entra ID -> Protection -> Conditional Access and create a new policy.
2. Create a new policy.
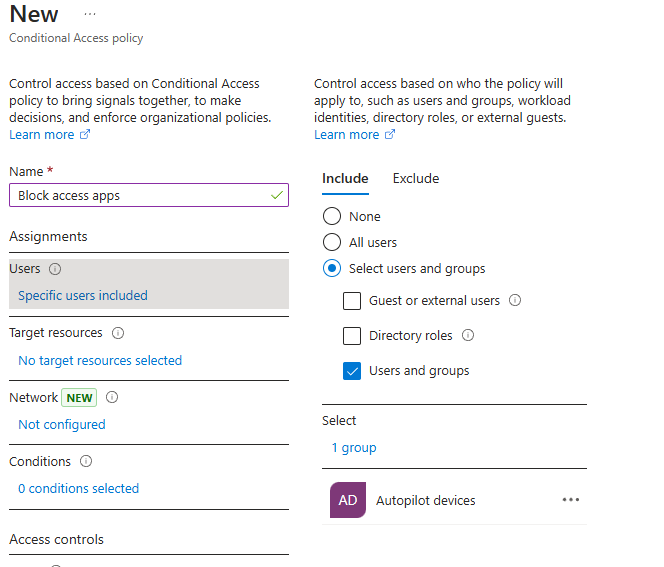
3. Give your policy a name and assign it to specific users/groups or apply it to all users.
.png)
If you apply the policy to all users, make sure to exclude the break-glass account. It's crucial to have a break-glass account for emergency access. Without it, a mistake could lock out all users, so ensure these accounts are excluded from the policy.
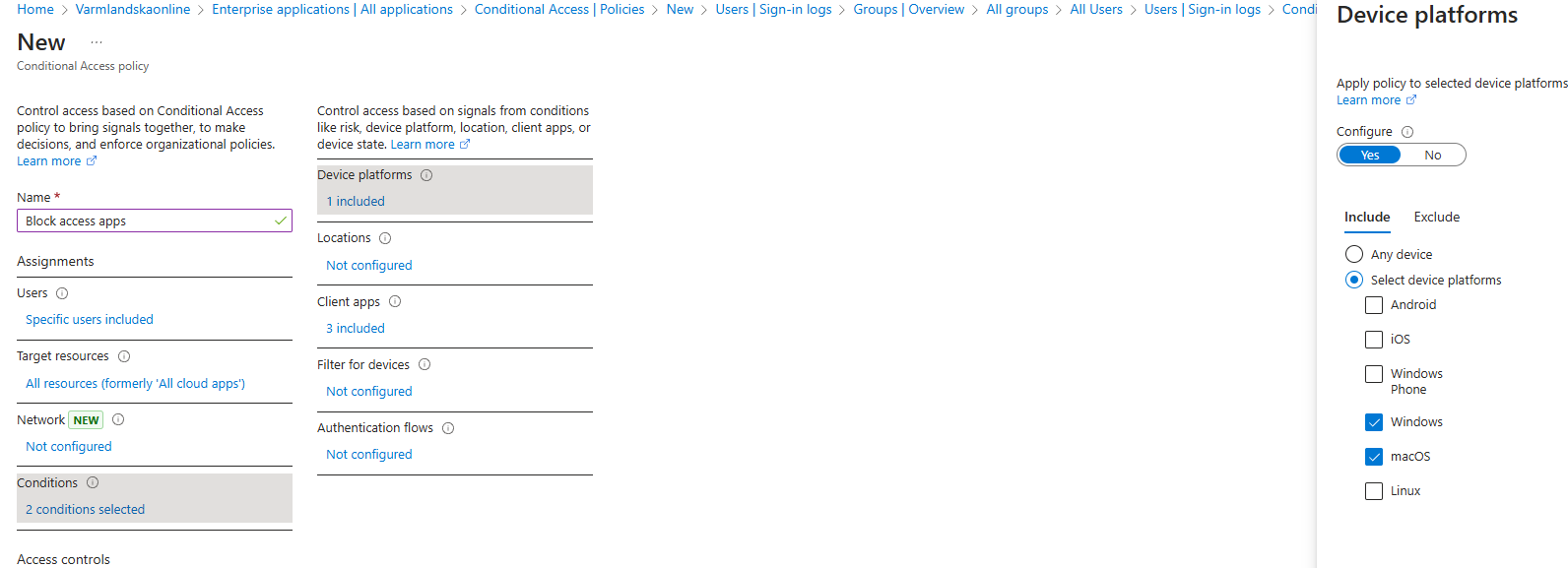
- In the "Target resources" section, choose "All resources" (previously known as "All cloud apps").
- Under conditions: Device platforms: Select the devices the policy should apply to. In my case, I will choose Windows and MacOS.
- Device platforms: Select the devices the policy should apply to. In my case, I will choose Windows and MacOS.
.png)
For Client apps, check all the boxes except "Browser," as this will block everything except browser access.
Here’s the key part: In the Filter for devices, you can use these filters: device.deviceOwnership -eq "Personal" -and device.deviceOwnership -ne "Company"
- Finally, under Grant, select Block.
- Enable the policy and save it.
Troubleshooting sign-in issues for users:
- Go to Entra ID and then navigate to Users.
- Select the user experiencing login issues.
- In the left panel, click on Sign-in logs.
- On the right panel, you'll see various options. Choose Conditional Access.
You can always check this option if users have failed to sign in, as the logs provide detailed information. However, be aware that it may take some time for the logs to appear.

